S3E2 – Data Brokers – Not so Anonymous
Hello, I’m Lydia Shompole and welcome to another episode of the Creepy Tech Podcast.
This week we are going to do a deep dive into data brokers. Lets discuss how information brokers collect, buy, sell and use your data and activity. Let’s jump right in!
Brokers:
According to the published definition a broker is a person or firm that buys and sells goods or assets for others. Brokers arrange or negotiate a settlement, deal, or plan.
Now, most of us are familiar with the term broker when applied to industries like the stock market. Stockbrokers have been working to assist individuals, and companies with managing their money, providing financial advice, or executing their transactions.
As new industries and technologies are created, we start to see existing services being applied in new and creative ways to meet newly created demand. In this case, the need for massive amounts of data created an entirely new job for brokers.
In 2014 the federal trade commission released the “Data Brokers – A Call for Transparency and Accountability” report that “examines and makes findings and recommendations with respect to the practices of data brokers—companies whose primary business is collecting personal information about consumers from a variety of sources and aggregating, analyzing, and sharing that information, or information derived from it, for purposes such as marketing products, verifying an individual’s identity, or detecting fraud”.
At the time, policy makers were concerned about the fast-paced emergence of new types of technology as well as the lack of transparency in how private or intimate consumer data was handled within these new companies.
This wasn’t the real beginning for data brokerage companies, but that doesn’t matter. What mattered was that their business practices had just caught the attention of not only the FTC and policy makers, but also the mainstream media and eventually us.
All of us had just received a front row ticket to the wild, wild west of data brokerage.
Data Galore:
Jumping ahead to an article from 2020 on WebFx.com which stated that “Today, there are over 4,000 data brokering companies worldwide. Acxiom, one of the largest, has 23,000 servers collecting & analyzing consumer data, Data for 500 million consumers worldwide, and up to 3,000 data points per person – and that’s just one company.”
This data contains information like:
Information collected by tracking cookies – I actually already covered that in the season 1 episode you can listen to that episode on any podcast app.
Website and email beacons – these are single pixel images that track your behavior on any websites, emails sent or received and a few other places. They collect information on what you click on, anywhere.
Browser fingerprinting – these are the use of special scripts (essentially code) that websites run to keep track of the type of browser you use, the default language used, as well as any other software you may have installed on the device. Now one interesting thing about your browser fingerprint is that there is currently no way for you to fully delete your fingerprint.
The financial Post also mentioned data brokers mine data from– “social media profiles, cellphone tracking, and offline milestones like marriage certificates, property deeds, driving records and court cases.” These are the money makers in the information industry.
And that’s not all, basically any service, app, or location you visit creates a data point about you, and these brokers want to collect, buy, sell, or use this data to help them make more money as quickly and easily as possible.
Not So Anonymous:
One main selling point that I’m sure we have all heard is that the data these companies collect is anonymized and since its anonymous, we shouldn’t care.
Well in 2019 Natasha Lomas wrote an article explaining that, “Researchers from two universities in Europe have published a method they say is able to correctly re-identify 99.98% of individuals in anonymized data sets with just 15 demographic attributes.”
Lomas cites additional studies performed that showed how easy it was to re-identify individuals from the anonymized data collected from them. The researchers from the 2019 study decided to also release the code they used for their study so that others could reproduce their results, and for those who want to test it out themselves but don’t want to use the actual code, they created a website where you can enter in information and see how likely it is that the data you enter can identify you.
I tested it out by entering 3 data points of my own, my date of birth, my gender and my zip code. Based on those 3 points it looks like there is a 55% chance that my answers would identify me. They also state that based on that percentage, “Other people have, on average, 83% chance of being correctly re-identified, making you much less unique than the rest of the US population.”
Now as their study stated, when they have 15 data points or attributes, they were able to re-identify an induvial 99.98% of the time. More attributes means a higher chance of picking you out of the bunch. Most companies ask for the basic 4 (name, date of birth, gender, email address or phone number).
The Experiment:
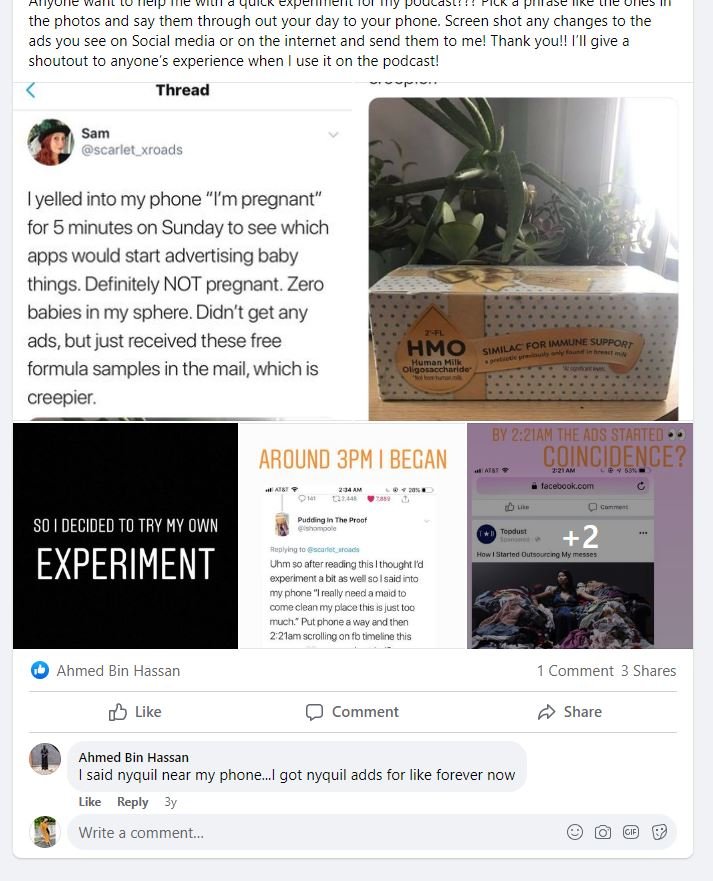
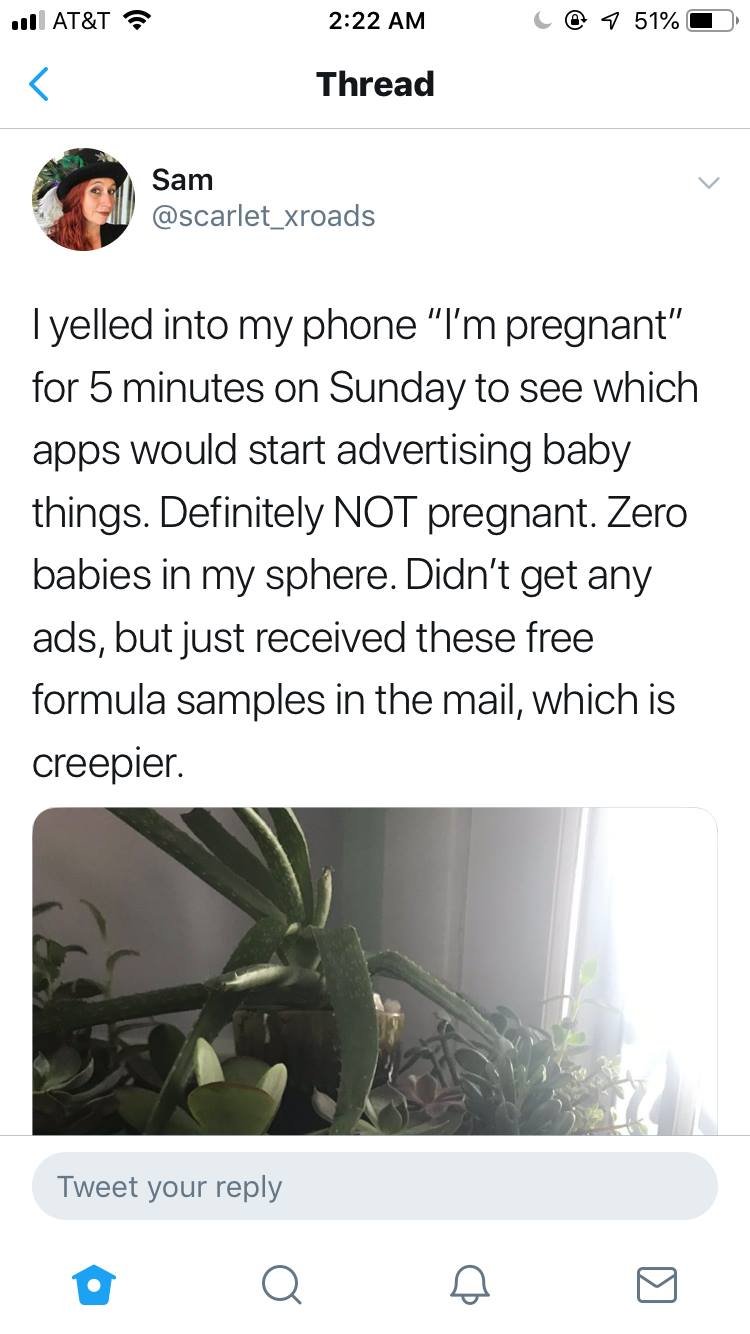
I’ve been interested in this topic for a while now, and on April 19th 2019 I saw a tweet posted by Scarlet_XRoads that inspired my first experiment to test whether or not these devices are actually listening to our conversations. A few days later I also asked anyone else out there to try it out as well and let me know what happened.
The tweet stated “ I yelled into my phone “I’m pregnant” for 5 minutes on Sunday to see which apps would start advertising baby things. Definitely NOT pregnant. Zero babies in my sphere. Didn’t get any ads, but just received these free formula samples in the mail, which is creepier.”
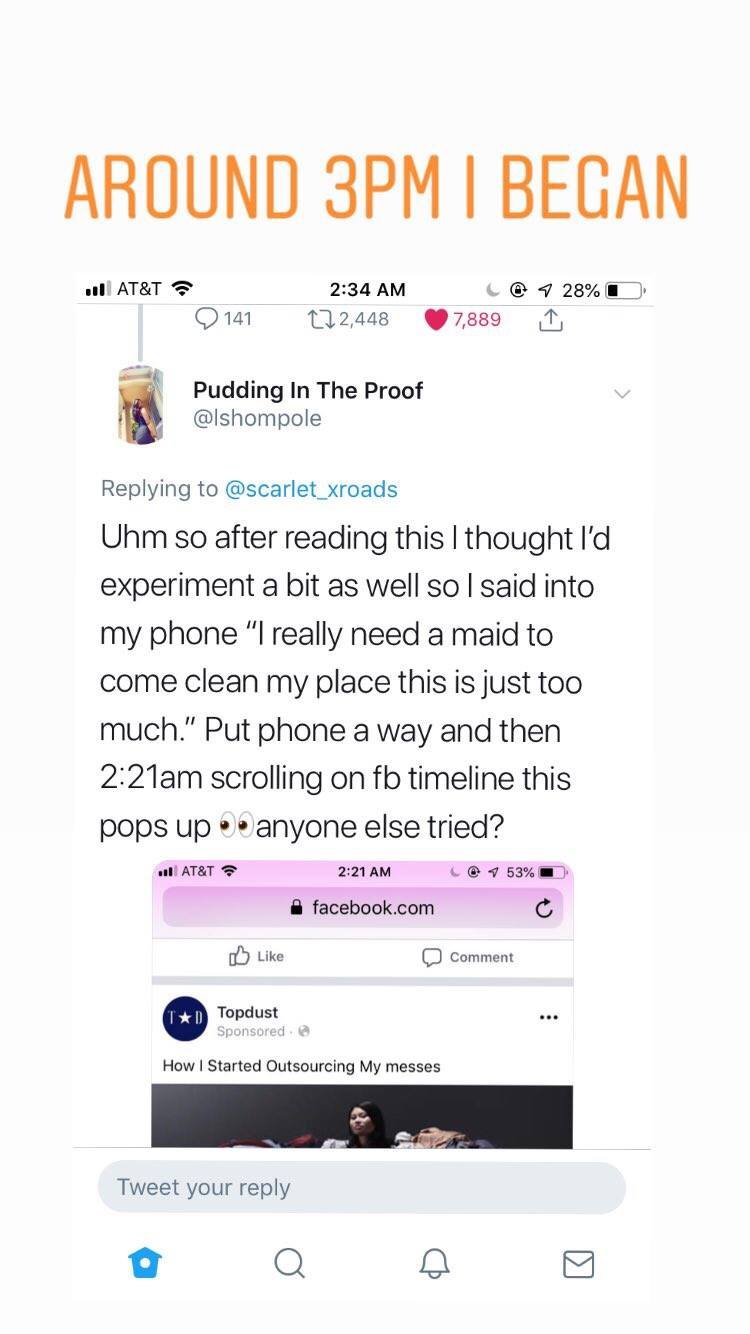
That same afternoon around 3pm, I decided to go ahead and test it out myself.
For my experiment, I selected a service that 1. Cannot afford, and 2. A service that I have never searched for, or viewed any content connected to the service. 3. I don’t even follow anyone who uses this service.
That afternoon around 3pm I repeated the following phrase every half hour or so and then would put my phone away. The phrase was “I really need a maid to come clean my place this is just too much”.
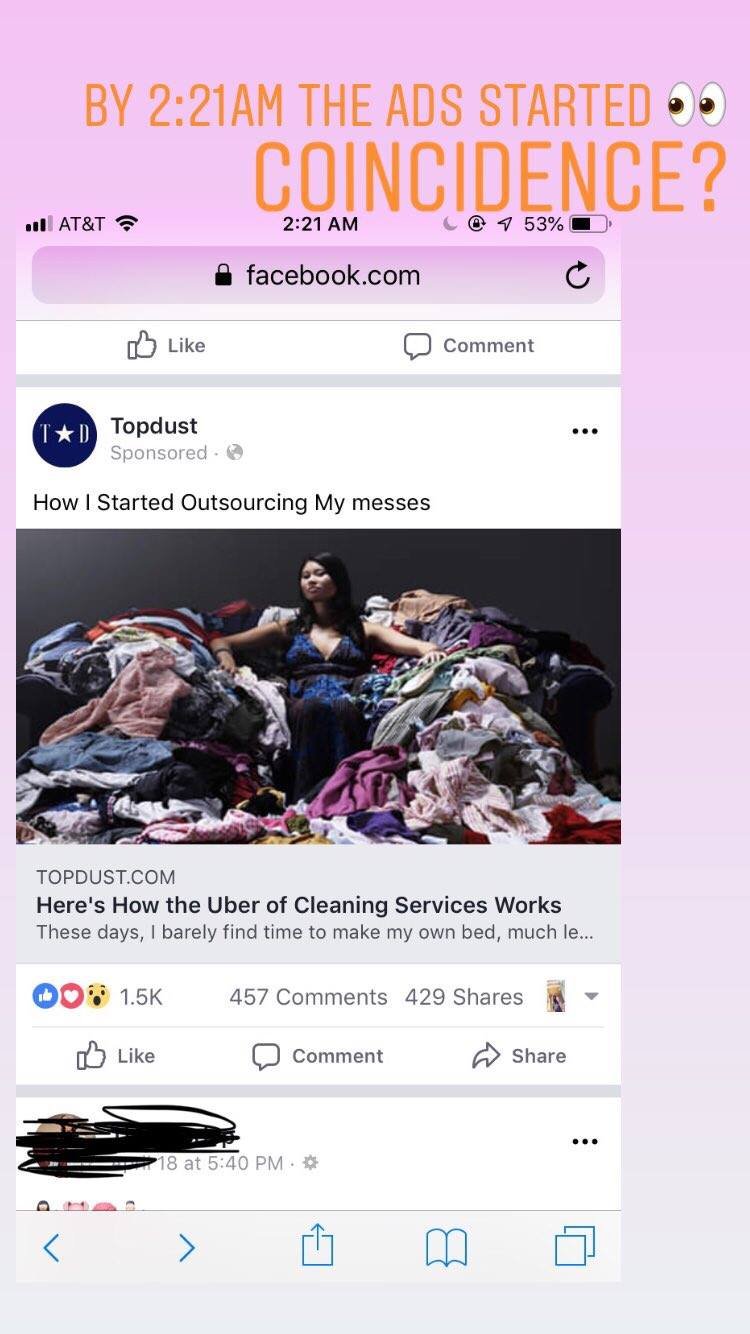
By 2:21am April 20th, 2019 I received the first advertisement on Facebook/Meta showing a business named Topdust with the headline “How I started Outsourcing My Messes” & the description of “ Here’s how the uber of cleaning services works. These days, I barely find time to make my own bed.”
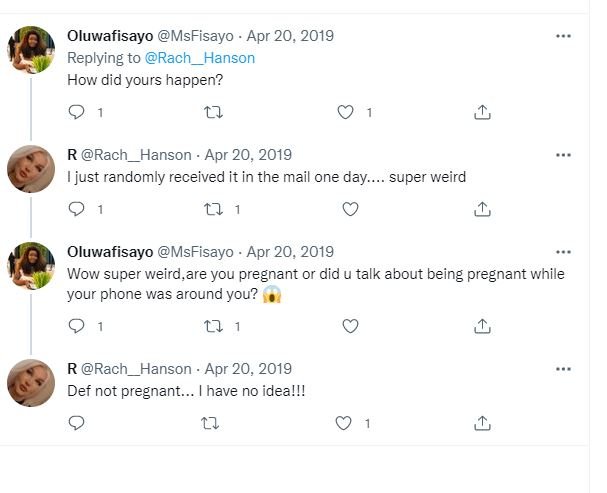
The results that others sent me or posted on the tweet/Facebook post also had similar results to Scarlet_XRoads and myself.
One person actually received samples of baby formula in the mail, while another individual started receiving and kept receiving advertisements for Nyquil. I’ve posted those screenshots to my website as well. Feel free to try this experiment out and let me know what happens.
After the experiment, I was curious to see if there was anyone else trying to figure out whether or not the data collected includes recordings of our day to day lives. A quick search produced the following from an article on Norton.com, yes, the antivirus company. The article stated that, “Yes, your phone is listening to you — to an extent and namely through virtual assistant apps, that is.”
When asked whether it’s legal, the article states that, “Yes, it is legal for phones to listen to you. That’s because we often give consent for phones to listen to us when we accept terms and conditions of software updates or app downloads.”
Taking Back Your Data:
Now what if you no longer want your life to be a set of data points used to market to you?
Well, there are a few things that you can start doing, but keep in mind that these are things that you will have to continue doing and they won’t completely stop your data from being collected. These things will just start to reduce the amount of data companies can accurately collect from you. Also, if you are a person whos’ work relies on customers finding you or your services online, then you should also know that taking these steps to minimize your footprint can/will affect your ability to work.
Delete or deactivate all accounts for shopping, social networks, and web services – yes, all of them. If you can’t delete completely (only deactivate) then make sure to replace all of your personal information in that account with fake information. That means, fake name, fake date of birth, fake addresses, email addresses, phone numbers, and also delete the posts or comments and messages you’ve made in that account. Once you change the email address and password, you will no longer have access to that account. So, make sure you do that last.
Search for all of the ways your information pops up online. You’ll then need to manually request removal of your data from the sites that you don’t want sharing or selling it – this one is super time consuming; I actually started this process towards the end of 2021, and it’s made a huge difference in reducing things like the number of spam emails I receive.
Delete old email accounts – and create a spam or online shopping email account that you only use for non-important matters
Change your privacy settings everywhere to restrict as much as possible.
If there is information you really don’t want to pop up, you can also ask Google for help. There is a right to be forgotten form that you can fill out. The right to be forgotten was established in May of 2014 in the European union giving individuals the right to ask Google to delist certain results related to their name. Keep in mind that Google reviews these requests on a case-by-case basis.
Start using a VPN all of the time, and please make sure it’s a paid VPN plan, you’ll have to also dig a little bit to research just how much data the VPN company is collecting about you.
There are a bunch of other things you would need to do continuously to make sure you aren’t giving away your information. I have linked a bunch of resources for you on my website.
Alright, that is all I have for you this week, if you find information that you’d love to share with me, feel free to message me what you found either by email, DM on socials or leaving a voice message on the creepy tech Anchor page...
As always, if you have a quick moment, head over to the apple podcast app and leave me a review. Let me know what you’d like me to cover this season.
You can follow me on IG @Tech_Creepy & on Twitter @TechCreepy & you can find the links I mentioned in this episode on my website Lshompole.com.
References:
https://privacyrights.org/resources/registered-data-brokers-united-states-2021
https://futurism.com/facebook-metaverse-vr-tracking
https://www.webfx.com/blog/internet/what-are-data-brokers-and-what-is-your-data-worth-infographic/
https://techcrunch.com/2019/07/24/researchers-spotlight-the-lie-of-anonymous-data/
https://www.wired.com/story/opinion-data-brokers-know-where-you-are-and-want-to-sell-that-intel/
https://futurism.com/facebook-metaverse-vr-tracking
https://financialpost.com/technology/data-brokers-are-tracking-you-and-selling-the-info
https://www.lshompole.com/creepy-tech/s2e2-my-cookies
https://twitter.com/lshompole/status/1119895653679656960
https://twitter.com/Rach__Hanson/status/1119629949294579713
https://www.topdust.com/handy-relationship2-2644832241.html
https://us.norton.com/internetsecurity-how-to-is-my-phone-listening-to-me.html
https://prospect.org/power/meet-stalkers/
https://techcrunch.com/2022/05/16/iccl-rtb-report-google-gdpr/
https://removaly.com/largest-data-brokers/
https://www.avast.com/c-data-brokers
https://smartsocial.com/post/social-media-clean-up
https://support.google.com/legal/answer/10769224?hl=en
https://www.nature.com/articles/srep01376
https://cpg.doc.ic.ac.uk/individual-risk/
https://techcrunch.com/2019/07/24/researchers-spotlight-the-lie-of-anonymous-data/
https://futurism.com/facebook-metaverse-vr-tracking
YouTube Videos:
60 Minutes: The Data Brokers – How Your Personal Information Is Sold Without Your Permission - https://www.youtube.com/watch?v=K1m_cigA988
Data Brokers: The Dark Industry of Selling Your Identity for Profit. - https://www.youtube.com/watch?v=wqn3gR1WTcA
Data Brokers: The Dark Industry of Selling Your Identity for Profit. - https://www.youtube.com/watch?v=uZ2l-kk5ihk
How data brokers sold my identity | Madhumita Murgia | TEDxExeter - https://www.youtube.com/watch?v=AU66C6HePfg
A data broker defends his industry - https://www.youtube.com/watch?v=NQmjbkASRIs
Opt-out your personal data from data broker sites - Privacy Monitor Assistant - https://www.youtube.com/watch?v=JGobZLKJyW0
This is how your Data is sold | Apps that don't collect your Data | Data Protection - https://www.youtube.com/watch?v=Hhyzx-rRBps
Deep Dive: What Are Data Brokers and How Do They Collect Your Data? - https://www.youtube.com/watch?v=rtYVB1AyFng
Photo credits:
Photo by Glen Carrie on Unsplash
Photo by Victoria Heath on Unsplash
Photo by Jeremy Bezanger on Unsplash
Photo by Maxim Hopman on Unsplash
Photo by Privecstasy on Unsplash
Photo by Claudio Schwarz on Unsplash
Photo by Markus Spiske on Unsplash
Hashtags:
#Privacy #DataProtection #DataSecurity